
Servers interpret received information very differently. It is known that %20 and +, when appeared in a parameter, are taken as a space symbol. A request for /folder/test/%2e%2e/page is normalized to /folder/page as %2e is an URL-encoded dot symbol. For example, the well-known open redirect works due to the request normalization.
However, a space symbol can become an attack. Let’s see how.
XBOX vulnerability
To begin with, there was a bug (not mine, but still funny). A 5 year old noted that he could get in his dad’s account by using a space character instead of a password! I am not really into the details of how this actually worked, but you can check out this link.
-Bo0oM, what do you have to do with this?
I was just wandering around when it turned out that I was on the same hall of fame with this guy and even got on TV!
Seen that?
You sure?
Look better!
Here it is:
Just for a third of a second… While scrolling. But still 🙂
Yandex subdomain vulnerability
It was noted that in basic circumstances, one of the subdomains on the /admin/ request requires a login:password pair:
http://sqtest.yandex.net/admin/ — 401
However, if a space symbol is added after admin, you were in w/o knowing any credentials.
http://sqtest.yandex.net/admin%20/ — 200
Links inside the admin panel required authentication information again, but if “/admin/“ was substituted for “/admin%20/“, one could use the admin panel easily. Unfortunately, there are no screenshots left so you have to believe me. The bug has been fixed, money received and already spent, only memories left.
Bitbucket Server vulnerability
Time passed, i had already forgotten the bug bounty vulnerability, but after another directory bruteforce I faced some weird behaviour, when /admin with a space symbol at the end returned 200 when it should have been a redirect to /login.
With a quick glance at the domain, it turned out that an application is a fresh version of the Bitbucket server. After opening the URL in the browser, I was amazed: I got an access to the admin panel (however, many links were not working).
Studying the Bitbucket server locally, I noticed that the server responds with the full data for the following links:
/admin%20/mail-server
/admin%20/db
/admin%20/db/edit
/admin%20/license
/admin%20/logging
/admin%20/server-settings
/admin%20/authentication
/admin%20/avatars
Looks funny, isn’t it?
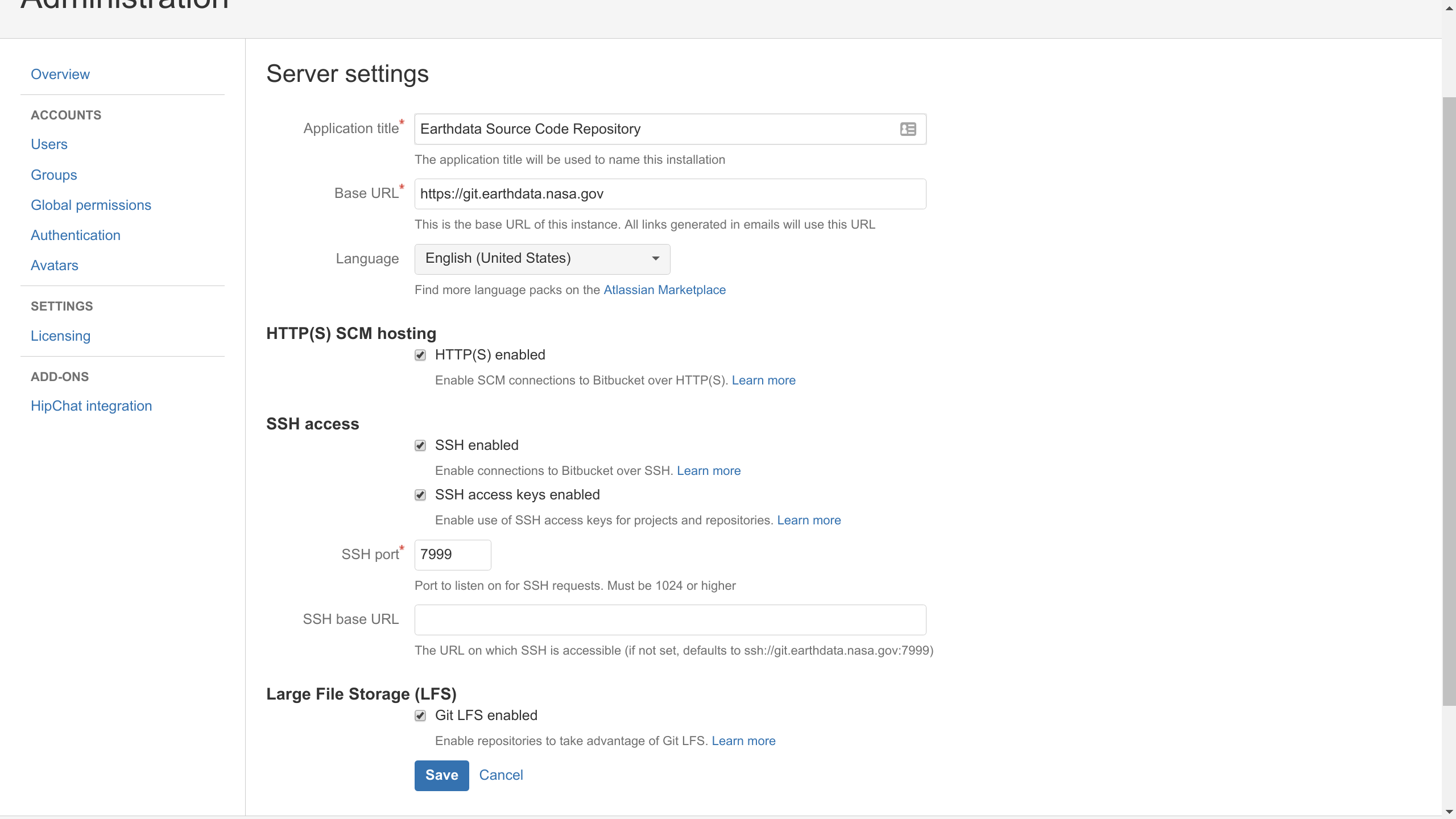
The vulnerability grants access to a limited number of directories, e.x. /admin/users/ is not accessible. Moreover, symbols x01-x20 could have been used to skip the authentication process.
Besides the directories listed above, list of plugins could have been exposed (the plugins can contain vulnerabilities too).
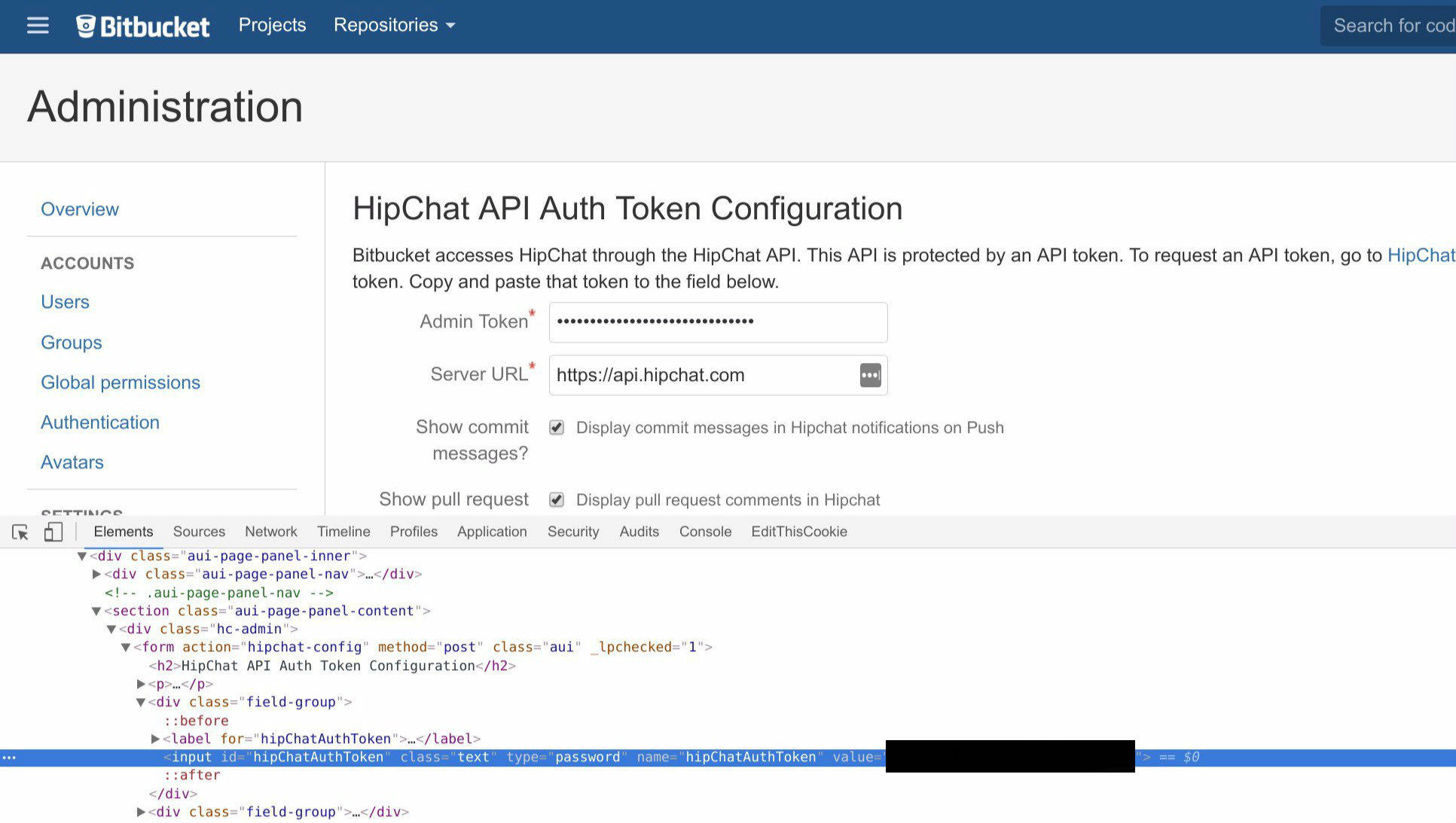
This bug has been fixed and deployed on Bitbucket Server > 4.8. Bitbucket is developed by the Atlassian team. They develop Jira, Confluence, Hipchat so, %username%, why don’t you study these products deeper? I could have missed something. Moreover, this bug can occur in other products too.
Translated by @easy_pwn